
Technical Resources
Educational Resources
APM Integrated Experience
Connect with Us
The security and privacy of your data is critically important to Loggly since you are placing your trust in our service. We want you to know that we’ve implemented security standards and operational processes using industry standards to protect your data today and into the future. This is an overview of our security practices, including how we handle your data from transmission, to storage, to access controls, and more.
Loggly gives your organization complete control over what data you send to our service. We don’t require you to install any agents, so we only receive data that you explicitly send to us. You may configure your applications and/or systems to forward the data you choose. It is transmitted securely to our cloud service using TLS.
Loggly maintains data in state-of-the-art facilities operated by Amazon Web Services (AWS) and Equinix.
To get access to the data, your team may log in to our secure web application through HTTPS. We give you control over which members of your organization have access, which sources of data they are allowed to see, and which settings they are allowed to change.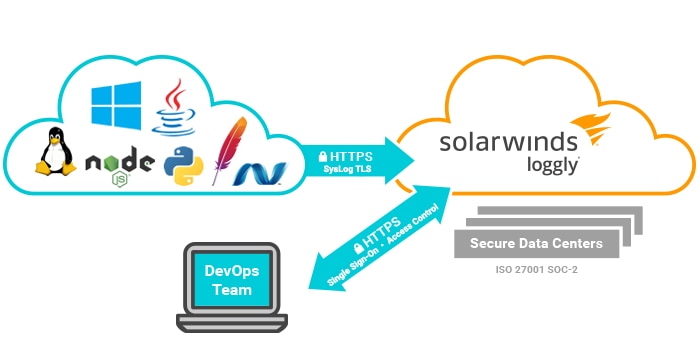
Loggly accepts data that is transmitted securely from your system to ours using Transport Layer Security (TLS). Data is encrypted using the latest SHA-256 certificate. We offer secure endpoints for both syslog and HTTPS, giving you a choice of protocol. Our endpoints also require the use of a unique customer token that is specific to each account. Tokens allow you to ingest data only from trusted sources. In the event a token is compromised, you can retire the compromised token and our system will stop accepting logs from it. Data which contains sensitive information can be filtered out before it leaves your premises. This can be done either in the application, syslog daemon, or logging agent. We offer configuration examples to scrub data matching specific patterns such as credit card numbers. Additionally, our collectors are configured with Cross Origin Resource Sharing (CORS) headers, allowing you to log data from browsers while your users are protected from cross site scripting (XSS) attacks.
As users access their data through the Loggly User Interface (UI), all interactions are held within secure sessions encrypted using TLS. Our Application Programming Interface (API) is also accessible through HTTPS and offers secure sessions. Each user account is authenticated using login credentials. We enforce best practices for password creation with rules including a minimum character count and use of uppercase characters and digits. We also offer our customers Federated Identity (FID) or Single Sign-On (SSO) through the use of SAML v2. This allows you to control your user authentication and authorization through your corporate directory. For example, users will be able to log in and receive a role assignment through their Active Directory (AD) credentials. Additionally, if your corporate identity provider allows multifactor authentication (2FA/MFA), you can turn it on to add more security to your accounts.
Each Loggly user is assigned a specific role that allows you to control which features and configuration settings each user is allowed to access. These roles and their privileges are described under User Roles and Privileges. Additionally, we offer granular control over which sources of data each user is allowed to view. This can be used to restrict access to sensitive information only to specific employees or partners.
Only Loggly administrators have access to the OS and application layer either on premise or through secured channels (e.g., VPN, ssh, etc). Loggly maintains an isolated private network where data processing and storage occur. Access to data within the Loggly network is only available through secured channels and follows the principles of least privilege in providing access between services, users, and data.
Loggly is SOC Type 2 Level 2 certified. Loggly can be used in environments regulated by PCI, HIPAA, and EU data protection. You can control what information is sent to Loggly, and filter or obfuscate regulated information like Personally Identifiable Information (PII) or credit card numbers. European customers should contact us to learn more about US-EU Standard Contractual Clauses (SCCs). Loggly also follows PCI best practices by encrypting our customers’ credit card information in transit, and we do not store the credit card information on our servers. All billing information is stored by our billing provider Braintree, which is a Level 1 PCI DSS Compliant Service Provider.
All your log data is automatically and permanently deleted at the end of your retention period. If you have chosen to enable our S3 archiving feature, you will have exclusive control over your bucket’s retention and security policies.
We take security incidents very seriously. We will investigate the issues and seek to resolve them quickly. When a security issue has the potential to affect our customers, we will follow industry best practices for disclosure and notification. If you have questions, suggestions, or believe you have identified a vulnerability, please contact us directly at info@loggly.com.
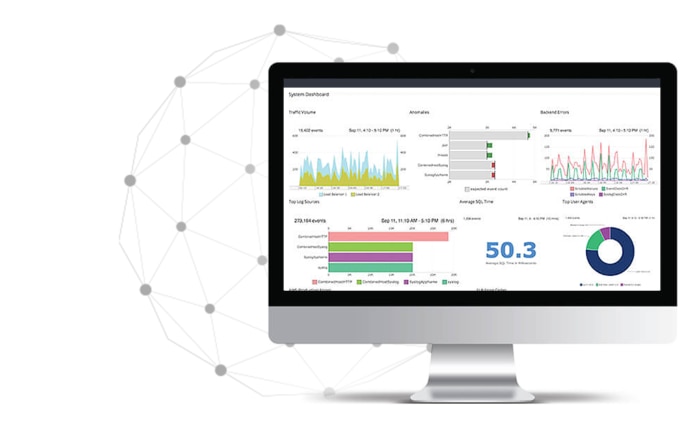
Monitor key resources and metrics, and eliminate small issues before they turn into big problems.
Trace issues down to their root cause by analyzing them in the context of the entire stack.
Analyze and visualize your data to answer key questions, track SLA compliance, and identify anomalies.
Work better as a team using data and analysis with DevOps tools. Loggly integrates with Slack, GitHub, Jira, PagerDuty, Microsoft Teams, custom webhooks and more.
Our multi-tenant SaaS provides a secure, fast, scalable, and highly available solution to meet the highest standards while keeping TCO low.