Technical Resources
Educational Resources
APM Integrated Experience
Connect with Us
Routers and firewalls are two of the most important devices in any network. Thanks to routers, you can provide network and internet connectivity to all devices. Firewalls then allow you to secure traffic. The network traffic flowing through these devices, and each connection will usually produce multiple log entries. This means these devices will produce many logs. Without a tool designed to aggregate and analyze these logs for you, it’s difficult to have a clear overview of what’s happening across your network. In this post, you’ll learn how to monitor and analyze firewall and router logs and how SolarWinds® Loggly® can help with this process.
Losing network connectivity completely is a clear sign of problems. What happens more often is a network seems to work fine, but the performance or the reliability of the connection is degraded. Different applications behave differently when they encounter network issues. Some will attempt to retry or reestablish connections, which means you won’t necessarily see there’s something wrong with the network. Here are a few examples of the most common use cases:
Another scenario where logs can help you find the issues is with configuration changes. When applying changes to the router or firewall, sometimes you may have problems even though the configuration looks correct. You double or triple check to confirm you configured particular functionalities according to the documentation, yet it doesn’t work properly. In this case, checking logs can point you to a source of the problem—usually, one functionality (which you may have configured properly) requires another functionality to be enabled or configured in a specific fashion.
Denied accesses or connections can create some confusion. There are different levels of blocked connections. With a firewall, you can simply block particular IP addresses or a range of addresses and/or ports, but you can also have some mechanisms enabled on the router to block connections. From the application/device perspective, it’s hard to distinguish what blocked the connection. Again, in these instances, checking the router and firewall logs will be the best way to quickly find the culprit.
Firewalls, by design, will block “suspicious” connections. These situations are not ideal and might even silently block a connection you specifically wanted to allow. Log messages will tell you about such actions. However, there may be different reasons for a firewall to mark such connections as “dangerous.” Therefore, it’s not always easy to find the root cause of a blockade. Aggregating and grouping logs per event can help you identify and fix that.
Because of the central role they play, routers and firewalls produce a large number of logs. The role can also allow any issue to cause connectivity disruption throughout the whole network. Therefore, it’s important to spot errors as soon as possible. Even better would be to spot problems before they’ll cause a critical issue. Sure, you can try to find these issues manually by searching error messages in the logs. And yes, you’ll eventually find them. But the bigger the network, the more complicated it becomes. It’s simply not an efficient way to do it. Also, you won’t be able to easily predict errors, detect anomalies, or do all other tasks requiring proper log analysis.
By using tools like Loggly, you’ll be able to act proactively instead of reactively. Instead of using logs to find the cause of the network issues, you’ll be able to use logs to constantly monitor the network, investigate problems, and fix upcoming problems before they cause serious issues.
In order to start analyzing logs with Loggly, you need to create an account and instruct the network device/service to ship logs to Loggly. Most routers and firewalls support syslog, which is also supported in Loggly. If necessary, you can also use other supported methods. After that, you’ll be able to benefit from centralized log analysis. Loggly has many features you can implement based on your needs. A few of them, however, can be used to improve the effectiveness of log analysis even more.
One of the most powerful features is anomaly detection—something almost impossible to do without tools like Loggly. Anomaly detection is important because it can help you solve smaller issues before they become bigger problems. A drastically increased number of connection retries can indicate an upcoming network issue. Increased network load outside of rush hours can indicate a DoS attack. Loggly can help you spot anomalies that don’t always lead to real problems but are always worth investigating.
Another important feature of a log management system is alerting. While anomaly detection can help in many cases, it won’t detect all the possible problems. Depending on the set threshold, however, alerts can also indicate something is going to go wrong in the future. While an issue like a broken network cable can’t be predicted early, thanks to alerting, you can be notified about many other issues as soon as possible. The sooner you know about an issue, the higher the chance you’ll be able to fix the problem before the user will notice it.
We tend to treat logs as a last step in the debugging process. But it’s also possible to create a dashboard based on data from the log messages, which will allow you to spot any problems even faster. It’s easier for a human to understand colors, graphs, and numbers than to read the whole line of text (line after line) By creating well-designed dashboards, you should be able to spot upcoming problems even before an alert gets triggered.
Predefined alerts and dashboards can drastically increase the effectiveness of your log analysis, but sometimes you need to find specific entries in the logs. Over time, you’ll probably end up searching for similar data. Saved searches are just that. Instead of wasting time typing the same queries multiple times, you can save the most commonly used queries once. Moreover, you can make them available for any user on your team.
We discussed the typical use cases for searching the logs of routers and firewalls. We also explained how using log management tools can supercharge the process. I provided a few example features of SolarWinds Loggly, but there are many more.
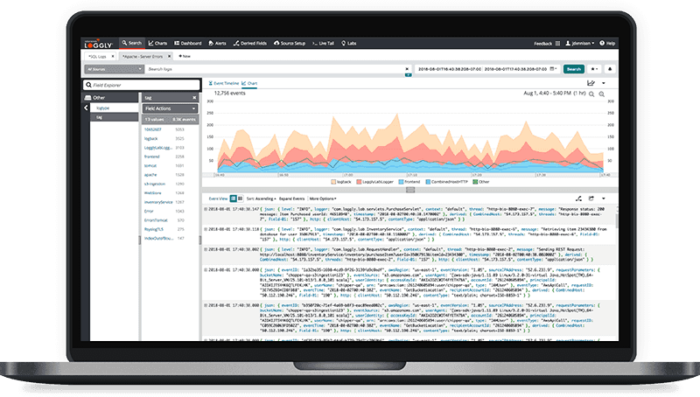
The most important thing to understand and remember is log analysis shouldn’t be considered as something extra. Of course, it’s not mandatory, and your systems will work without it. But, as we explained in this post, log analysis allows you to spot problems faster. When done properly, you can even prevent several issues before they become serious. Log analysis will help to keep your network in a healthy state.
This post was written by David Ziolkowski. David has 10 years of experience as a network/system engineer at the beginning, DevOps in between, cloud native engineer recently. He’s worked for an IT outsourcing company, a research institute, telco, a hosting company, and a consultancy company, so he’s gathered a lot of knowledge from different perspectives. Nowadays he’s helping companies move to cloud and/or redesign their infrastructure for a more cloud native approach.